|
How to create Self-signed Certificates for Hyper-V Replica - Step by step with screenshots
Before we start, we need to download Makecert.exe from Microsoft website.
On the Windows Server 2012 A (Primary Server)
1. Open command line with administrator right.
2. Run this command to Create a self-signed root authority
certificate
makecert -pe -n "CN=PrimaryTestRootCA" -ss root -sr LocalMachine -sky
signature -r "PrimaryTestRootCA.cer"
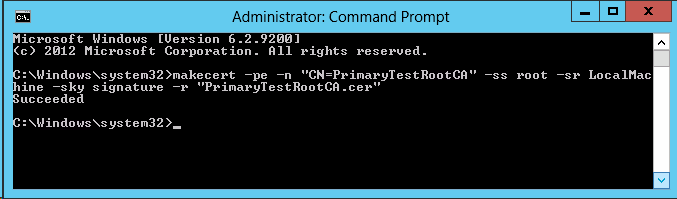
Note: The PrimaryTestRootCA.cer will be copied to
C:\Windows\system32 or
C:\Windows\sysWOW64 depending
on the OS.
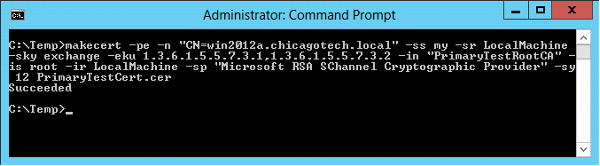
3. Run this command to create a new certificate signed by the test root
authority certificate
makecert -pe -n "CN=<FQDN>" -ss my -sr LocalMachine -sky exchange -eku
1.3.6.1.5.5.7.3.1,1.3.6.1.5.5.7.3.2 -in "PrimaryTestRootCA" -is root -ir
LocalMachine -sp "Microsoft RSA SChannel Cryptographic Provider" -sy 12
PrimaryTestCert.cer
Replace <FQDN> with the Windows Server A FQDN, for example
makecert -pe -n "CN=win2012a.chicagotech.local" -ss my -sr LocalMachine -sky
exchange -eku 1.3.6.1.5.5.7.3.1,1.3.6.1.5.5.7.3.2 -in "PrimaryTestRootCA"
-is root -ir LocalMachine -sp "Microsoft RSA SChannel Cryptographic
Provider" -sy 12 PrimaryTestCert.cer
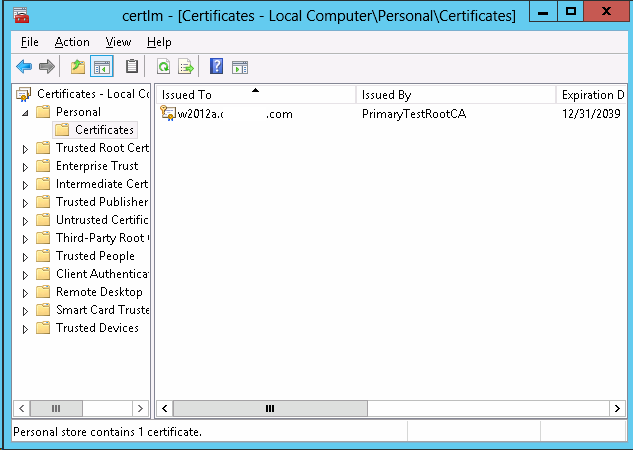
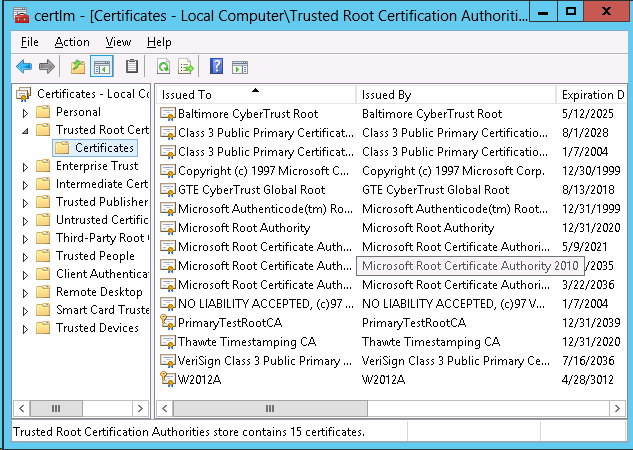
4. Verify the certificate has been created on the Certificate Local Computer
(both Personal and Trusted Root Certification).
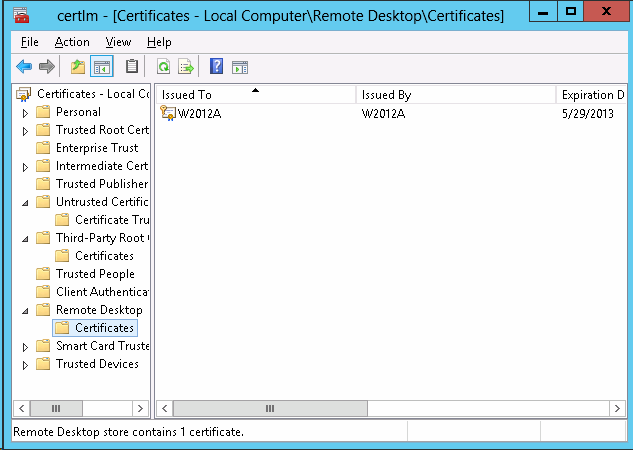
On the Windows Server B (Recovery or Replica Server)
1. Run command line with administrator rights.
2. Run this command to Create a self-signed root authority certificate
makecert -pe -n "CN=RecoveryTestRootCA" -ss root -sr LocalMachine -sky
signature -r "RecoveryTestRootCA.cer"
3. Run this command to create a new certificate signed by the test root
authority certificate
makecert -pe -n "CN=<FQDN>" -ss my -sr LocalMachine -sky exchange -eku
1.3.6.1.5.5.7.3.1,1.3.6.1.5.5.7.3.2 -in "RecoveryTestRootCA" -is root -ir
LocalMachine -sp "Microsoft RSA SChannel Cryptographic Provider" -sy 12
RecoveryTestCert.cer
Replace <FQDN> with the Windows Server B FQDN, for example,
makecert -pe -n "CN=win2012b.chicagotech.local" -ss my -sr LocalMachine -sky
exchange -eku 1.3.6.1.5.5.7.3.1,1.3.6.1.5.5.7.3.2 -in "RecoveryTestRootCA"
-is root -ir LocalMachine -sp "Microsoft RSA SChannel Cryptographic
Provider" -sy 12 RecoveryTestCert.cer
Finishing Up
1. Copy "RecoveryTestRootCA.cer" (Located in
C:\Windows\system32 or
C:\Windows\sysWOW64) from the Replica
server to the Primary and import by running the following command elevated
certutil -addstore -f Root "RecoveryTestRootCA.cer"
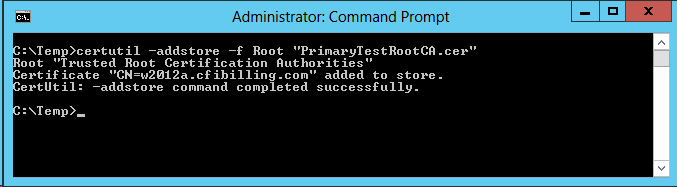
2. Copy "PrimaryTestRootCA.cer" from the Primary server to the Replica and
import by running the following command elevated
certutil -addstore -f Root "PrimaryTestRootCA.cer"
1.
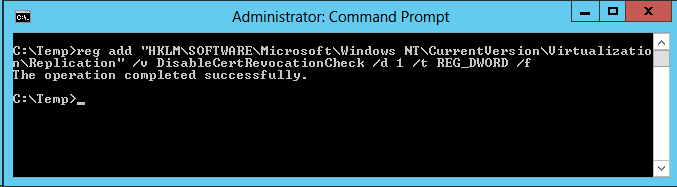
3. By
default, a certificate revocation check is mandatory and Self-Signed
Certificates donít support Revocation checks. Hence, both modify the
following registry key on both the Primary and Replica servers to disable
the CRL check
reg add "HKLM\SOFTWARE\Microsoft\Windows
NT\CurrentVersion\Virtualization\Replication" /v DisableCertRevocationCheck
/d 1 /t REG_DWORD /f
Post your questions, comments, feedbacks and suggestions
Contact a consultant
Related Topics
|

This web is provided "AS IS" with no warranties.